(1) How to remove Windows Ultimate Security Patch?
(Copied from: http://www.2-viruses.com/remove-windows-ultimate-security-patch)
What is Windows Ultimate Security Patch?
Although the name Windows Ultimate Security Patch is new for most of internet users, yet if one has a closer look,
he will see that it is only the latest rogue antivirus released by FakeVimes family. Its only goal is to earn money
by tricking naive computer users into spending their salaries on buying a licensed version of Windows Ultimate Security Patch.
How does it work? You will see its signs very quickly. Your work with a computer will be interrupted by a list of
alerts. Note: these alerts are false. The only aim of them is to trick you into clicking on the ads and subsequently
purchasing a licensed Windows Ultimate Security Patch version. It plays with your fear that your PC is infected but
don’t get caught by this game. The only wise step is to remove Windows Ultimate Security Patch. This will guarantee
that you get rid of computer viruses and bothersome alerts.
A computer gets installed with Windows Ultimate Security Patch after Trojan infection through PC security vulnerabilities.
This rogue is programmed the way that it starts running as soon as a user reboots his computer. Your work will be interrupted
by warning messages similar to the below:
Warning
Warning! Identity theft attempt detected!
Hidden connection IP: 87.23.232.71
Target: Your bank account details
Your IP: 127.0.0.1
Recommended :
Please click “Prevent Attack” button to prevent all attacks and protect your PC.
It is quite interesting that Windows Ultimate Security Patch knows what data is targeted… as it is nearly impossible to
determine automatically. Especially if you are not doing online banking at that time.
Warning! Spambot detected!
Attention! A spambot sending viruses from your e-mail has been detected on your PC.
Warning
Firewall has blocked a program from accessing the Internet
C:\program files\internet explorer\iexplore.exe
is suspected to have infected your PC. This type of virus intercepts entered data and transmits them to a remote server.
why Windows Ultimate Security Patch finds it strange that Internet explorer connects to internet?
Torrent Alert
Recomended: Please use secure encryption protocol for torrent links.
Torrent link detected!
Receiving this notification means that you have violated the copyright laws. Using Torrent for downloading movies and licensed software shall be prosecuted and you may be sued for cybercrime and breach of law under SOPA legislation.
Please register your copy of the AV to activate anonymous data transfer protocol through torrent link.
Get Anonymous connection
From the examples above you may see that Windows Ultimate Security Patch uses strong wording to frighten a computer user and make him
purchase its fake license. One may choose to ignore the message but these do get annoying and interrupt work every time rebooting a computer.
The simplest solution is to remove Windows Ultimate Security Patch without any delay. Be sure to use reliable removal tools and
run a full system scan with licensed anti-malware versions, such as Spyhunter or Spyware Doctor (2012 version). If you choose
manual route for removing Windows Ultimate Security Patch, do not forget to repair registry rules related to antiviruses.
These rules make your PC defenseless against future infections. (11:38 AM 5/30/2012)
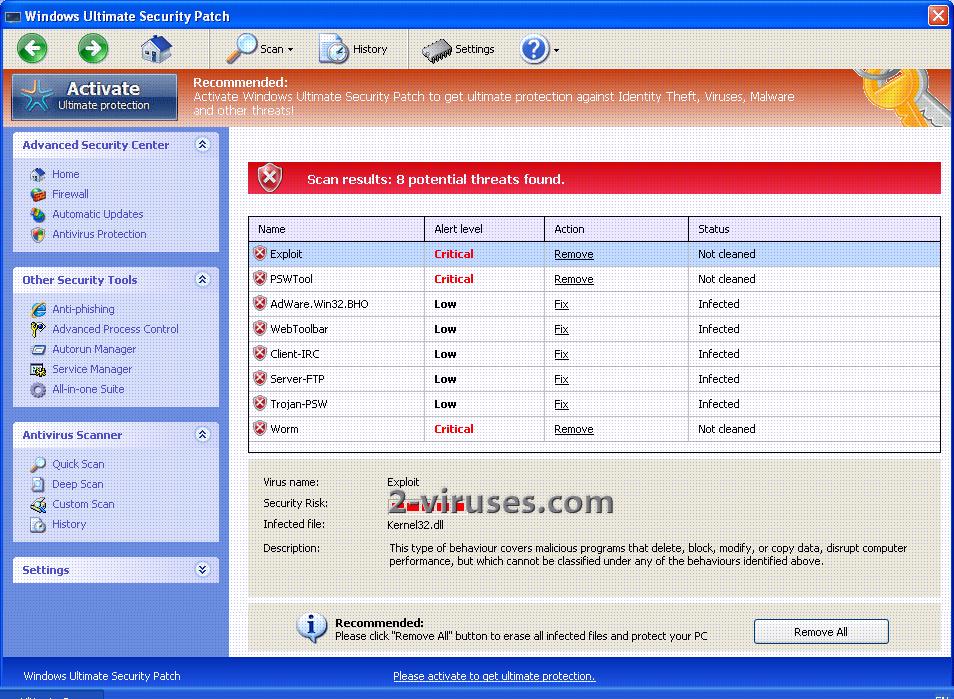
Screenshot of Windows Ultimate Security Patch
Manual Windows Ultimate Security Patch removal
Stop these Windows Ultimate Security Patch processes:
Protector-[rnd].exe
Remove these Windows Ultimate Security Patch Registry Entries:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\
Inspector = %AppData%\Protector-[random].exe
HKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\a.exe\Debugger = svchost.exe
HKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\aAvgApi.exe\Debugger = svchost.exe
HKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\AAWTray.exe\Debugger = svchost.exe
HKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\About.exe\Debugger = svchost.exe
HKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\ackwin32.exe\Debugger = svchost.exe
HKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\Ad-Aware.exe\Debugger = svchost.exe
HKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\adaware.exe\Debugger = svchost.exe
HKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\advxdwin.exe\Debugger = svchost.exe
HKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\AdwarePrj.exe\Debugger = svchost.exe
HKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\agent.exe\Debugger = svchost.exe
HKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\agentsvr.exe\Debugger = svchost.exe
HKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\agentw.exe\Debugger = svchost.exe
HKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\alertsvc.exe\Debugger = svchost.exe
HKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\alevir.exe\Debugger = svchost.exe
HKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\alogserv.exe\Debugger = svchost.exe
HKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\AlphaAV\Debugger = svchost.exe
HKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\AlphaAV.exe\Debugger = svchost.exe
Remove these Windows Ultimate Security Patch files:
Protector-[rnd].exe in %AppData% folder
It is impossible to list all file names and locations of modern parasites. You can identify remaining parasites, other Windows
Ultimate Security Patch infected files and get help in Windows Ultimate Security Patch removal by using free Spyhunter scanner. It comes with
free real-time protection module that helps preventing Windows Ultimate Security Patch and similar threats.
Windows Ultimate Security Patch is classified as Rogue Application. After infecting a user’s system, it proceeds to scare its victim into buying
the “product” by displaying fake messages, stating that your computer need particular components, or need to be fixed or has other serious problem
that needs only Windows Ultimate Security Patch can help you to solve these after you download the trial version. As soon as the victim downloads
Windows Ultimate Security Patch trial version, it offers to buy the full version to fix these false errors. If the user agrees, Windows Ultimate
Security Patch not only does not fix the errors, but it takes the user’s money and may even install additional spyware into the victim’s computer.
Some Rogue Applications, such as Windows Ultimate Security Patch, may offer users to buy it after the victim clicks on a banner or a pop-up while
surfing the internet. Usually, a Trojan is installed to a victim’s computer after clicking on the advertisement, or comes bundled with various
freely shiped programs like codecs. It then proceeds to download or even install Windows Ultimate Security Patch, which is another way for Rogue
application to spread itself.
(2) Windows Ultimate Security Patch manual remover:
(Copied from: http://trojan-killer.net/windows-ultimate-security-patch-virus-removal/)
Delete Windows Ultimate Security Patch files:
%AppData%\NPSWF32.dll
%AppData%\Protector-[rnd].exe
%AppData%\result.db
Delete Windows Ultimate Security Patch registry entries:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\Inspector %AppData%\Protector-[rnd].exe
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\WarnOnHTTPSToHTTPRedirect 0
HKCU\Software\Microsoft\Windows\CurrentVersion\Settings\ID 4
HKCU\Software\Microsoft\Windows\CurrentVersion\Settings\UID [rnd]
HKCU\Software\Microsoft\Windows\CurrentVersion\Settings\net [date of installation]
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\ConsentPromptBehaviorAdmin 0
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\ConsentPromptBehaviorUser 0
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\EnableLUA 0
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AAWTray.exe
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AAWTray.exe\Debugger svchost.exe
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVCare.exe
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVCare.exe\Debugger svchost.exe
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVENGINE.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVENGINE.EXE\Debugger svchost.exe

